CodeQL zero to hero part 2: getting started with CodeQL
CodeQL Zero to Hero Part 2: Getting Started with CodeQL
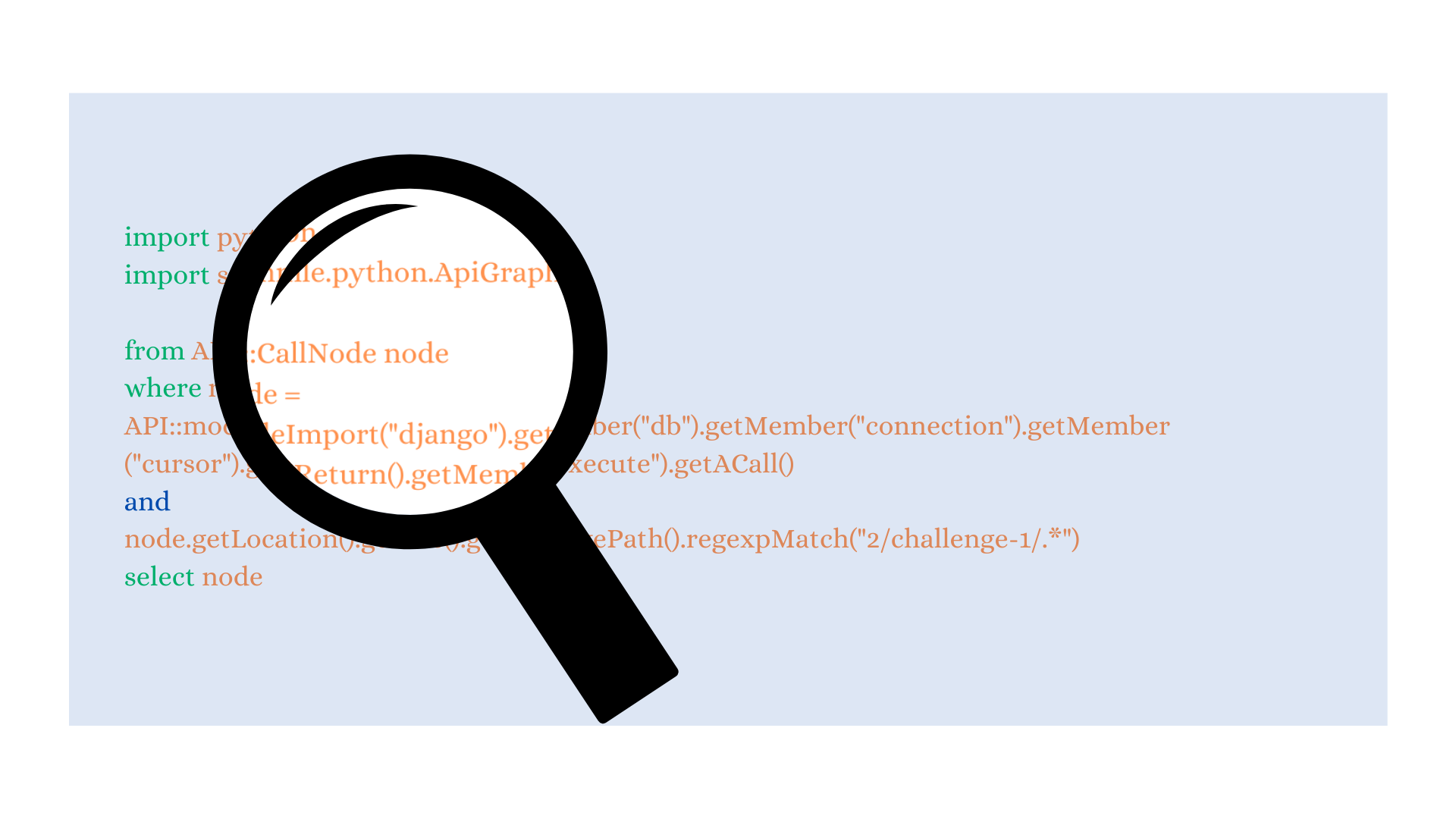
This blog post focuses on getting started with CodeQL, a static analysis tool for vulnerability research. CodeQL analyzes code as data and uses a special query language, called QL, to query the database for vulnerable patterns. The post covers how to write CodeQL queries and enable code scanning with CodeQL in a public repository. Advantages of using CodeQL for security research include automatic scanning of code for vulnerabilities and insights into potential issues in a codebase.
Recapping the Fundamentals
The post begins with a recap of fundamental concepts in vulnerability research, such as sources, sinks, data flow analysis, and taint analysis. These concepts are used in many static analysis tools, including CodeQL.
Using CodeQL
CodeQL has several uses, including automated scanning of code for hundreds of vulnerability types. Once a vulnerability is found in a codebase, CodeQL can be used to search for other instances of the vulnerability in different parts of the codebase.
Code Scanning with CodeQL
The easiest way to try out CodeQL is by enabling code scanning with CodeQL on a repository. The post includes a challenge to enable code scanning with CodeQL on a fork of a vulnerable code repository.
Advantages of Code Scanning with CodeQL
The post highlights the advantages of using code scanning with CodeQL as a security researcher. Code scanning with CodeQL can be done automatically for most languages and will rebuild and reanalyze codebase changes quickly. CodeQL can also provide insights into potential issues in a new codebase for research.
Conclusion
Overall, this blog post provides a helpful introduction to CodeQL and how to get started with it for vulnerability research.